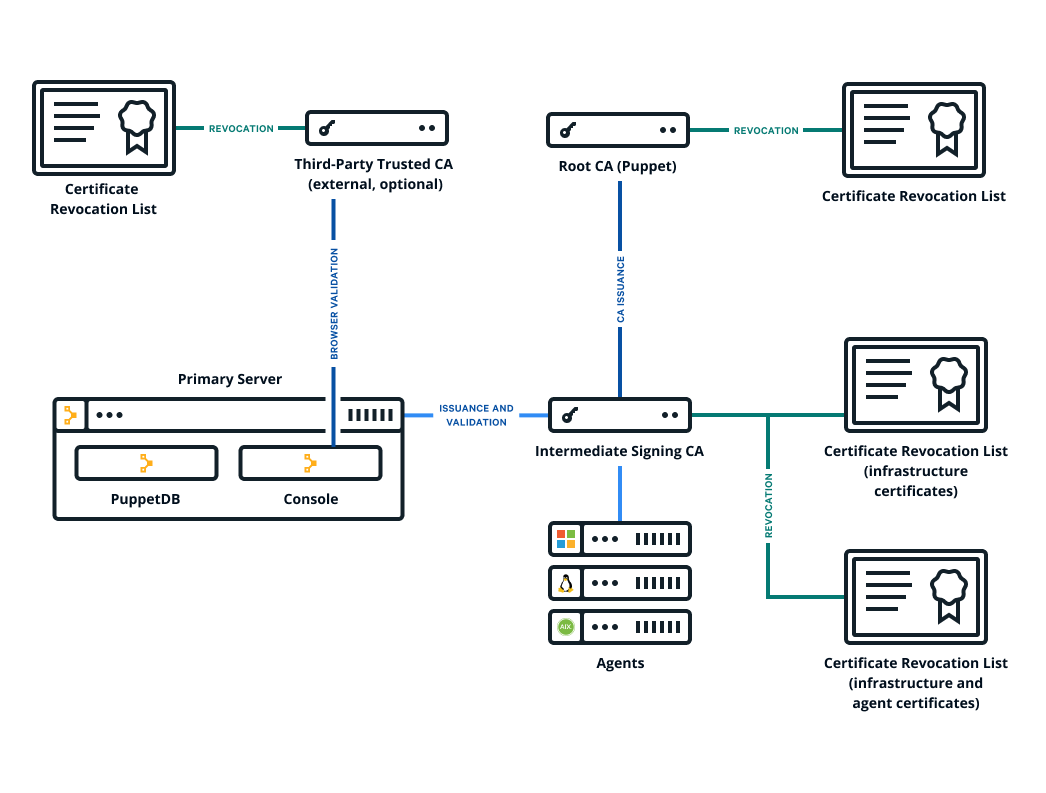
The Puppet Enterprise (PE) console uses a certificate signed by
PE's built-in certificate authority (CA). Because this CA is
specific to PE, web browsers don't know it or trust it, and you
have to add a security exception in order to access the console. If you find that this is not
an acceptable scenario, you can use a custom CA to create the console's
certificate.
Before you begin
- You need a X.509 cert, signed by the custom party CA, in PEM format, with matching
private and public keys.
- If your custom cert is issued by an intermediate CA, the CA bundle must contain a
complete chain, including the applicable root CA.
- These keys and certs must be in PEM format.
-
Retrieve the custom certificate and private key.
-
Move the certificate to
/etc/puppetlabs/puppet/ssl/certs/console-cert.pem, replacing any
existing file named console-cert.pem.
-
Move the private key to
/etc/puppetlabs/puppet/ssl/private_keys/console-cert.pem, replacing any
existing file named console-cert.pem.
-
If you previously specified a custom SSL certificate, remove any
browser_ssl_cert and browser_ssl_private_key parameters specified in the console or Hiera data.
In the console, go to the Node groups page, expand the
PE Infrastructure group, and select the PE
Console node group. Then, on the Classes tab,
locate the puppet_enterprise::profile::console class,
remove any browser_ssl_cert and browser_ssl_private_key parameters, and commit
changes.
If you declared these parameters on the Configuration data
tab, remove them from that tab and commit changes.
-
Run Puppet:
puppet agent
-t
Results
You can navigate to your console and see the custom certificate in your browser.
