System configuration
Before installing Puppet Enterprise, make sure that your nodes and network are properly configured.
Network considerations
Before installing, consider these network requirements
Timekeeping
Use NTP or an equivalent service to ensure that time is in sync between your primary server, which acts as the certificate authority, and any agent nodes. If time drifts out of sync in your infrastructure, you might encounter issues such as agents recieving outdated certificates. A service like NTP (available as a supported module) ensures accurate timekeeping.
Name resolution
Decide on a preferred name or set of names that agent nodes can use to contact the primary server. Ensure that the primary server can be reached by domain name lookup by all future agent nodes.
You can simplify configuration of agent nodes by using a CNAME record to make the primary server
reachable at the hostname puppet, which is the default primary
server hostname that is suggested when installing an agent node.
Web URLs used for deployment and management
PE uses some external web URLs for certain deployment and management tasks. You might want to ensure these URLs are reachable from your network prior to installation, and be aware that they might be called at various stages of configuration.
| URL | Enables |
|---|---|
| forgeapi.puppet.com | Puppet module downloads. |
| pm.puppetlabs.com | Agent module package downloads. |
| s3.amazonaws.com | Agent module package downloads (redirected from pm.pupptlabs.com). |
| rubygems.org | Puppet and Puppet Server gem downloads. |
| github.com | Third-party module downloads not served by the Forge and access to control repositories. |
Antivirus and antimalware considerations
Antivirus and antimalware software can impact or prevent the proper functioning of
PE. To avoid issues, exclude the directories /etc/puppetlabs and /opt/puppetlabs from antivirus and antimalware tools that scan disk write
operations.
- Exclude the
/etc/puppetlabsand/opt/puppetlabsdirectories from antivirus and antimalware tools that scan disk write operations to avoid performance issues. - Some antivirus and antimalware software requires a lot of system processing power. Tune your system resources (infrastructure nodes) to accommodate the software so it doesn't slow your performance.
- Some antivirus and antimalware software defaults to using port 8081, which is the same port PuppetDB uses. When installing the software, consider which port it uses so it doesn't conflict with PuppetDB communications.
- For agents, you can exclude
C:\ProgramData\PuppetLabs\pe_patchif your antivirus is holding a lock on log files and causing patching failures.
Firewall configuration
Follow these guidelines for firewall configuration based on your installation type.
Firewall configuration for standard installations
The port requirements for standard installations are described.
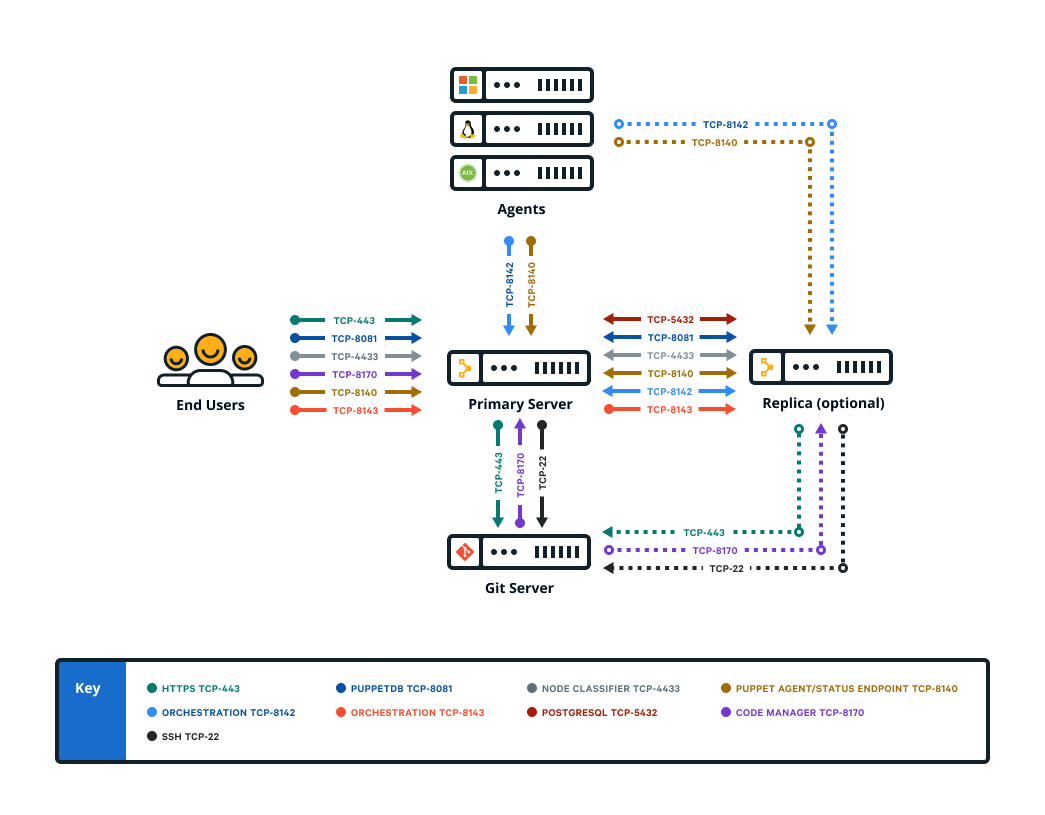
| Port | Use | Virtual private networks for cloud deployments |
|---|---|---|
| 22 |
|
External |
| 443 |
|
External |
| 4433 |
|
External |
| 5432 |
|
Internal |
| 8081 |
|
Internal |
| 8140 |
|
Internal |
| 8142 |
|
Internal |
| 8143 |
|
Internal |
| 8170 |
|
Internal |
Firewall configuration for large installations
These are the port requirements for large installations with compilers.
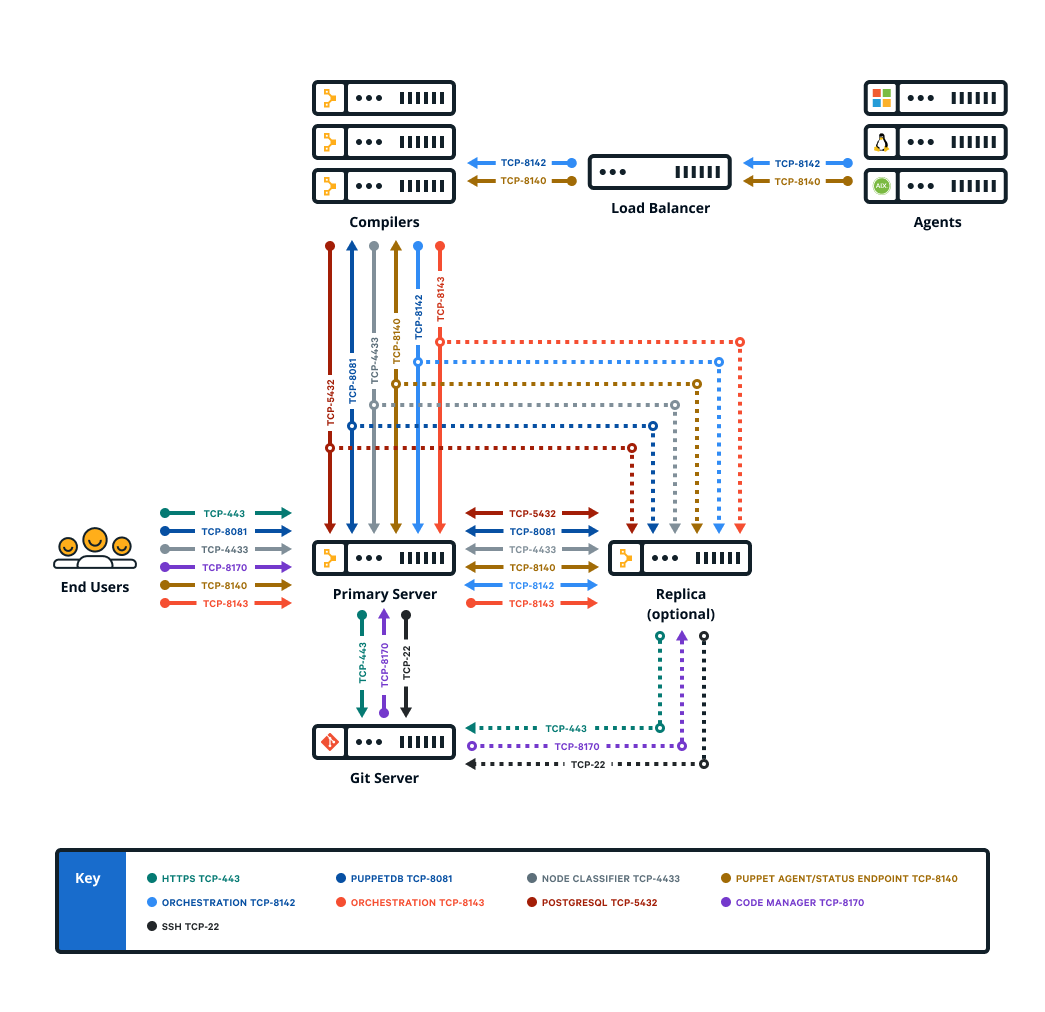
| Port | Use |
|---|---|
| 22 |
|
| 443 |
|
| 4433 |
|
| 5432 |
|
| 8081 |
|
| 8140 |
|
| 8142 |
|
| 8143 |
|
| 8170 |
|
Firewall configuration for extra-large installations
These are the port requirements for extra-large installations with compilers.
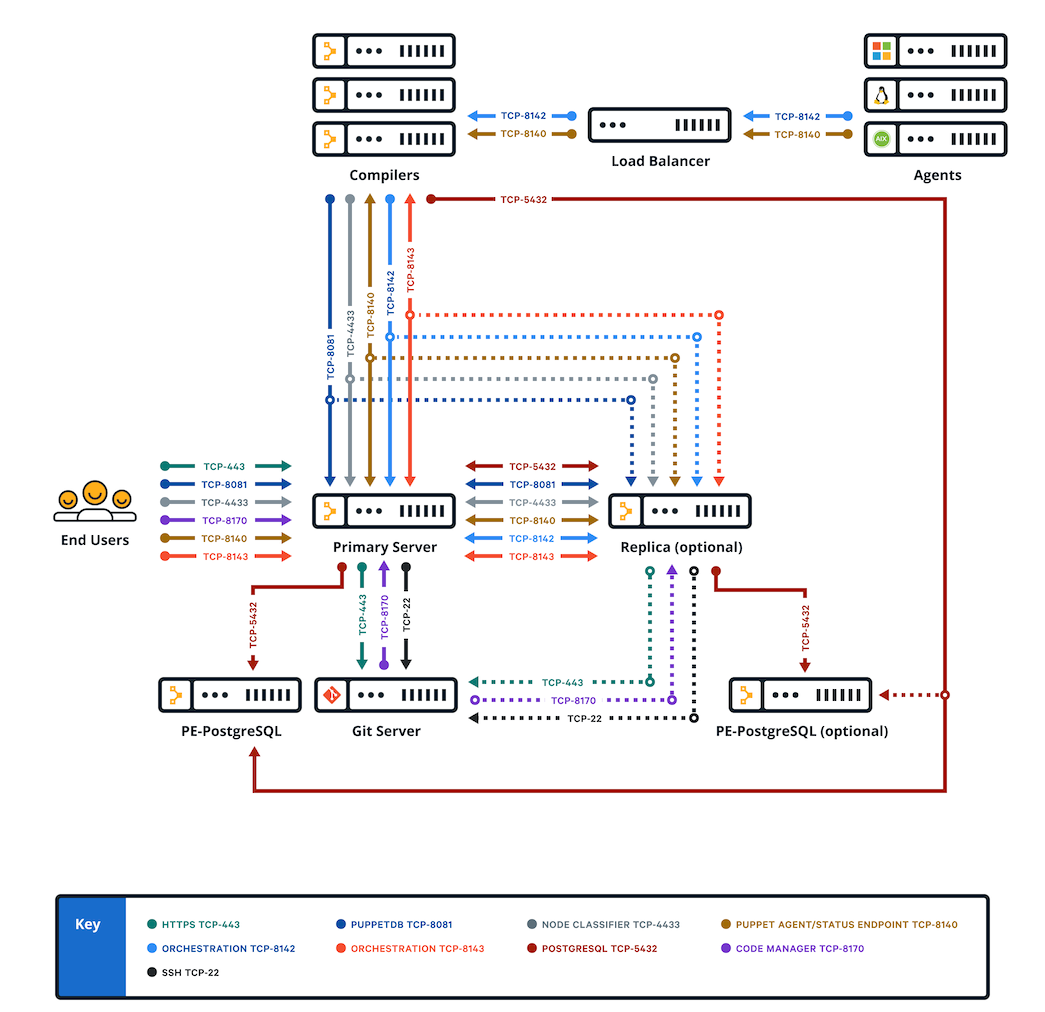
| Port | Use |
|---|---|
| 22 |
|
| 443 |
|
| 4433 |
|
| 5432 |
|
| 8081 |
|
| 8140 |
|
| 8142 |
|
| 8143 |
|
| 8170 |
|
Firewall configuration for standalone PE-PostgreSQL installations
These are the port requirements for installations with compilers and standalone PE-PostgreSQL
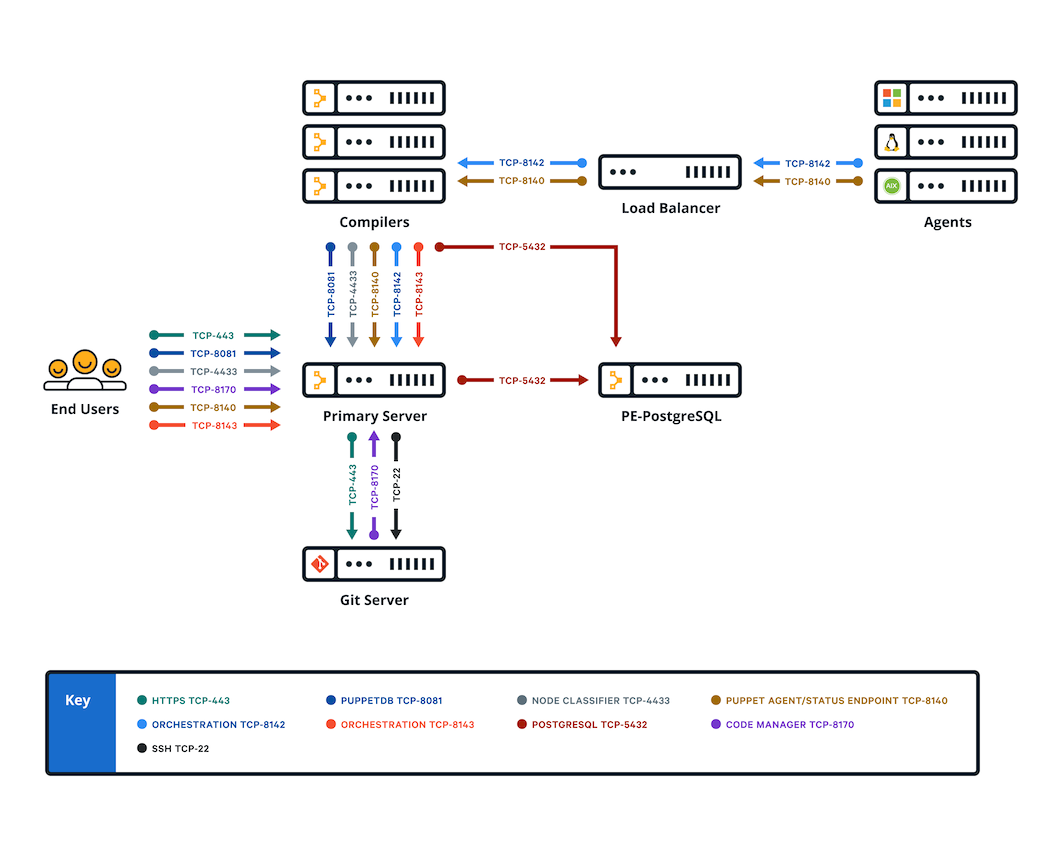
| Port | Use |
|---|---|
| 22 |
|
| 443 |
|
| 4433 |
|
| 5432 |
|
| 8081 |
|
| 8140 |
|
| 8142 |
|
| 8143 |
|
| 8170 |
|