Use a custom SSL certificate for the console
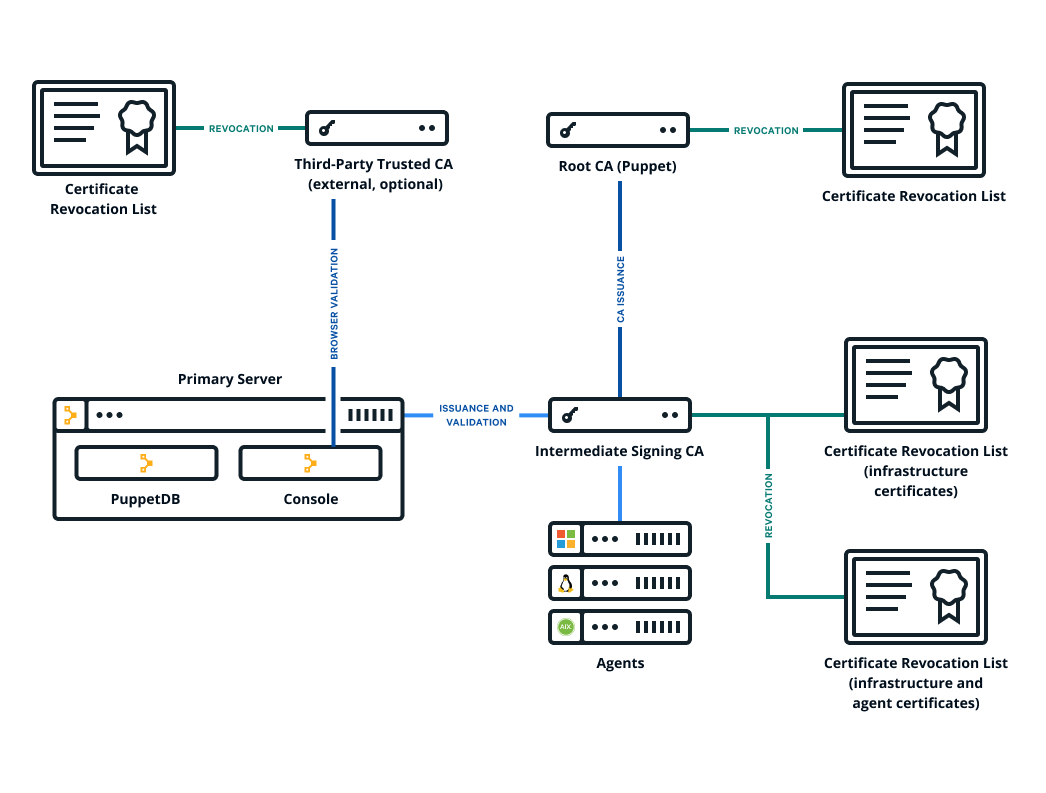
The Puppet Enterprise (PE) console uses a certificate signed by PE's built-in certificate authority (CA). Because this CA is specific to PE, web browsers don't know it or trust it, and you have to add a security exception in order to access the console. If you find that this is not an acceptable scenario, you can use a custom CA to create the console's certificate.
Before you begin
- You need a X.509 cert, signed by the custom party CA, in PEM format, with matching private and public keys.
- If your custom cert is issued by an intermediate CA, the CA bundle must contain a complete chain, including the applicable root CA.
- These keys and certs must be in PEM format.
Results
You can navigate to your console and see the custom certificate in your browser.
Related information