Accelerate Vulnerability Remediation for Proactive Risk Reduction
Eliminate patching delays and protect your IT systems from known vulnerabilities and threats. Vulnerability Remediation in Puppet Enterprise Advanced integrates with your preferred scanner to identify and prioritize risk. Empower your teams to address known vulnerabilities more consistently and efficiently.
Accelerate Remediation & Unify Teams to Increase Efficiency
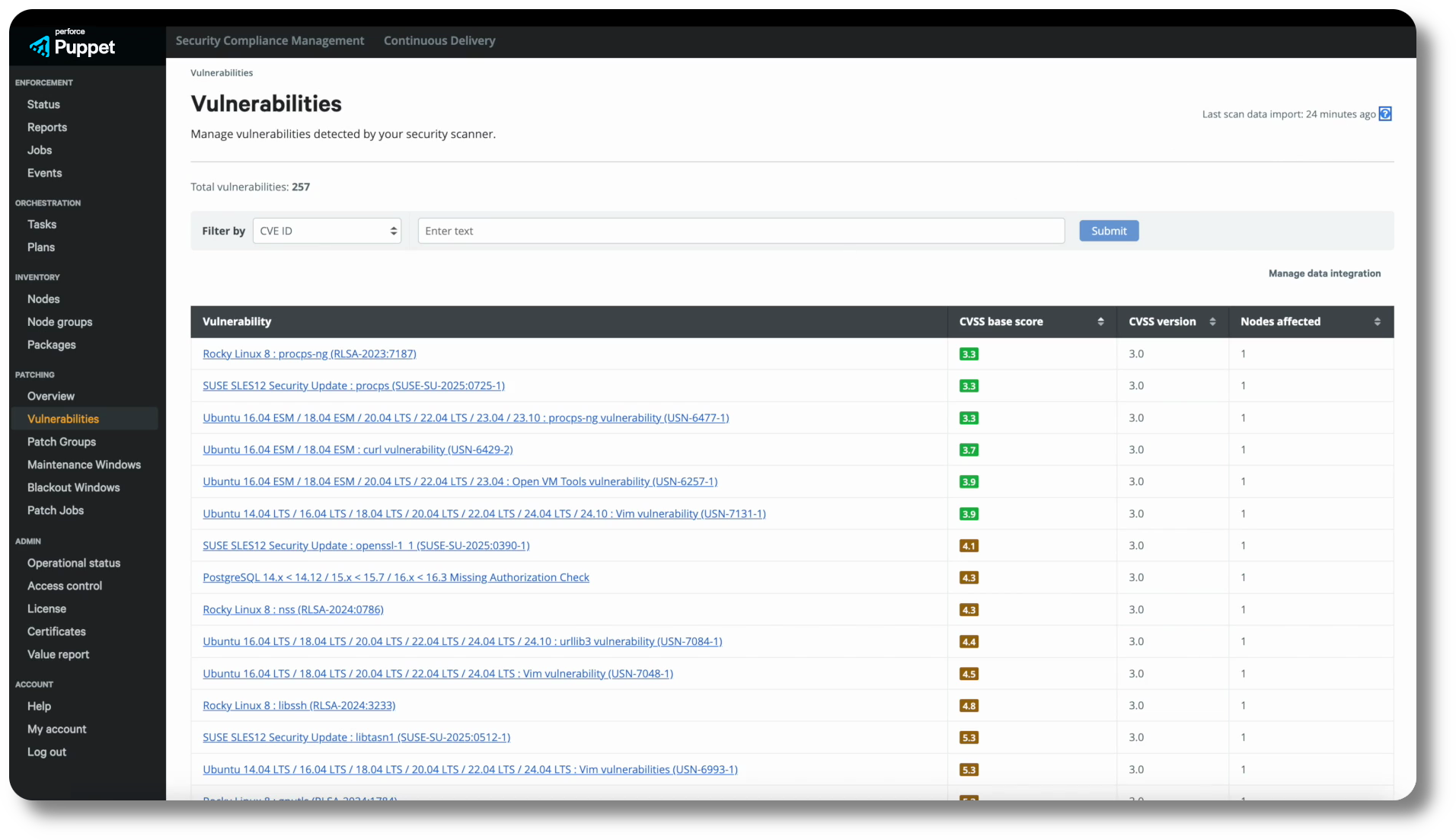
Ingest Vulnerability Data
Integrate with Nessus and other popular security scanners by leveraging our open integration framework.
- Leverage the power of your chosen security scanning tool.
- Directly ingest security scan data and avoid the dreaded cross-functional handoff.
- Improve coordination between security and platform teams and eliminate bottlenecks with self-service.
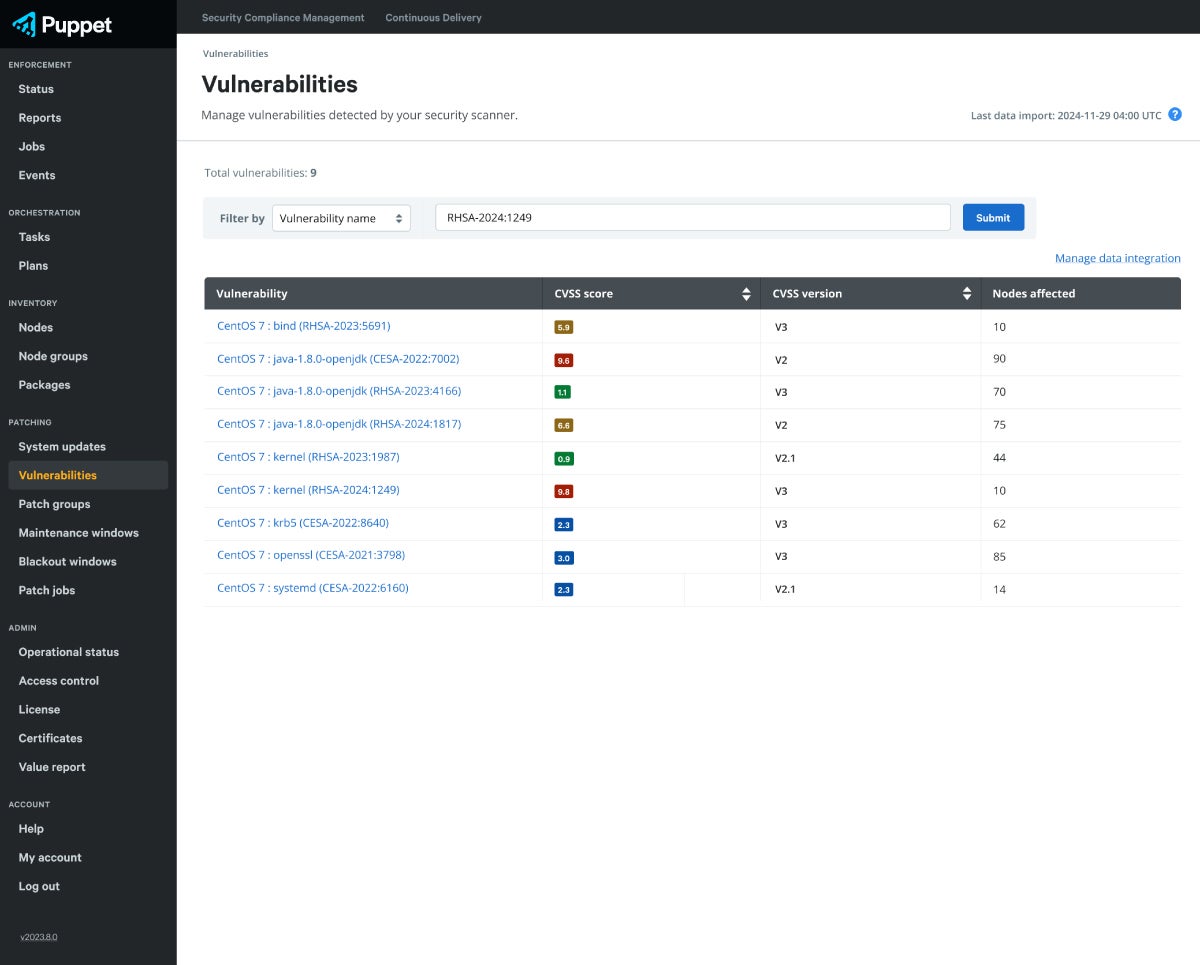
Assess Impact
View important information about vulnerabilities directly in the Puppet Enterprise console and plan remediation without juggling different tools.
- Quickly determine which Puppet Enterprise managed nodes are at risk from known vulnerabilities.
- View detailed information about each vulnerability, including CVSS scores.
- Sort according to CVSS scores to prioritize remediation based on criticality.
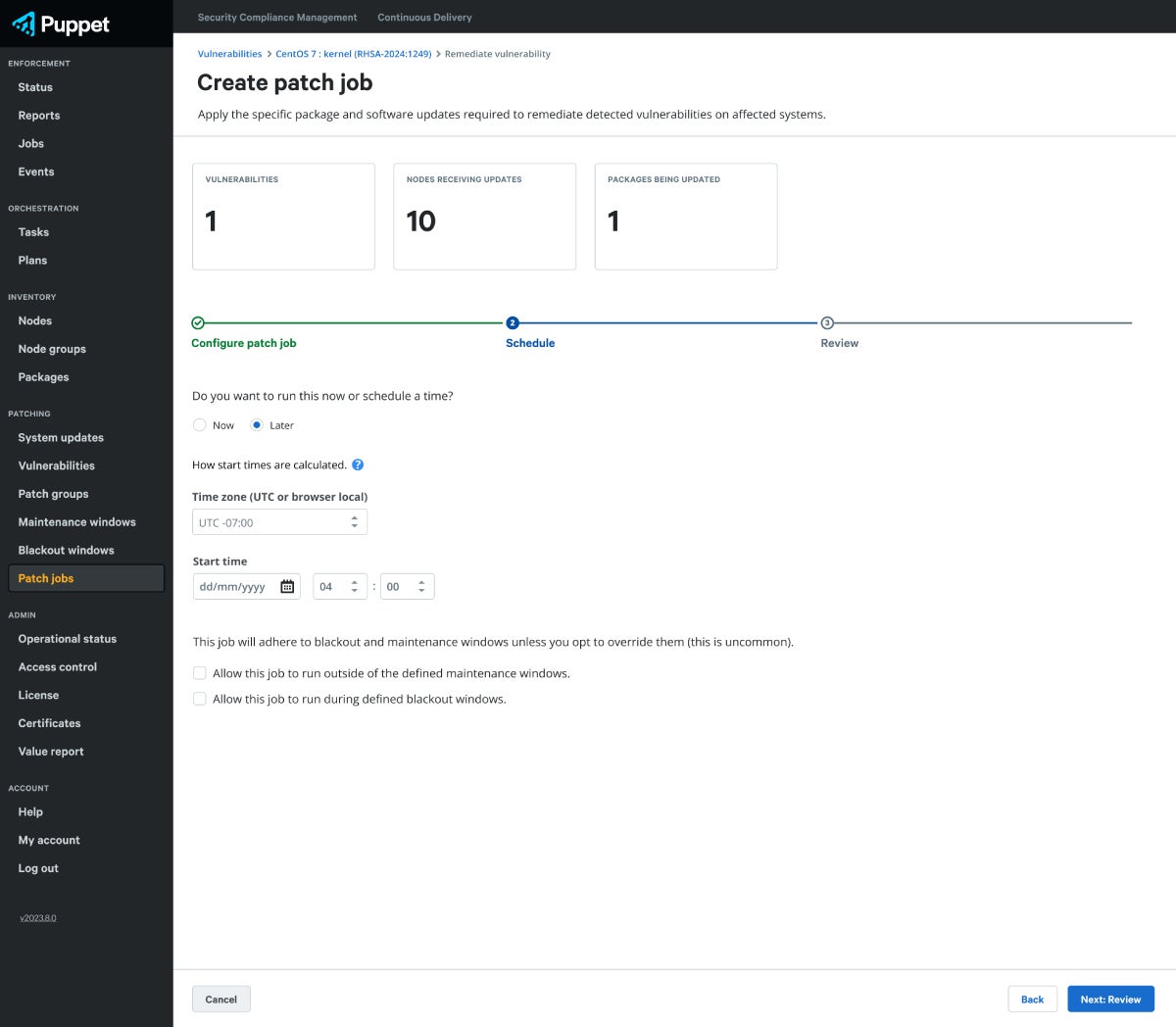
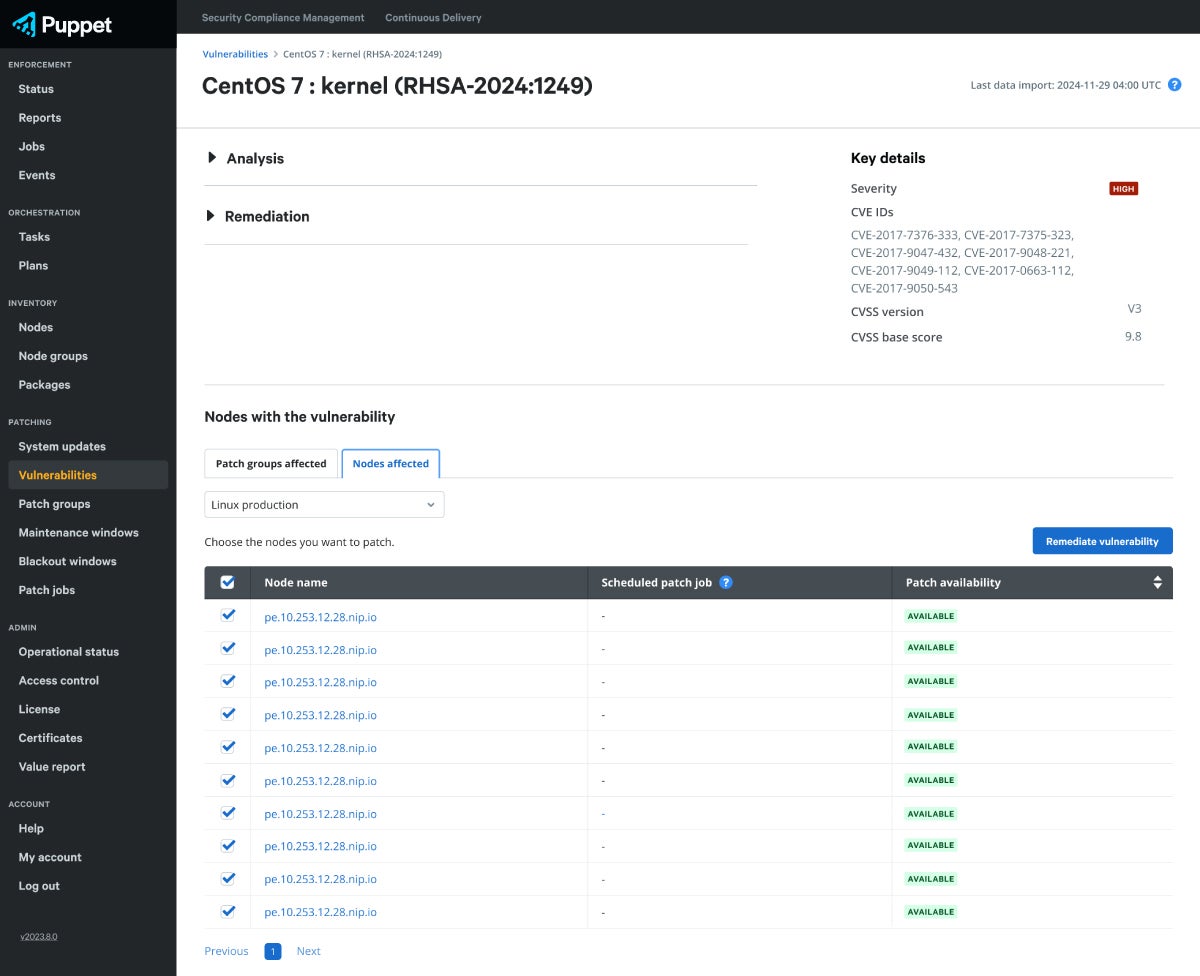
Automate Remediation
Address vulnerabilities by applying the required updates to the affected nodes with time saving automation.
- Deploy patches individually or at scale without disrupting critical business operations using maintenance and blackout windows.
- Manage user access with granular functionality control using RBAC.
- Reduce the time to remediate vulnerabilities using powerful Puppet automation.
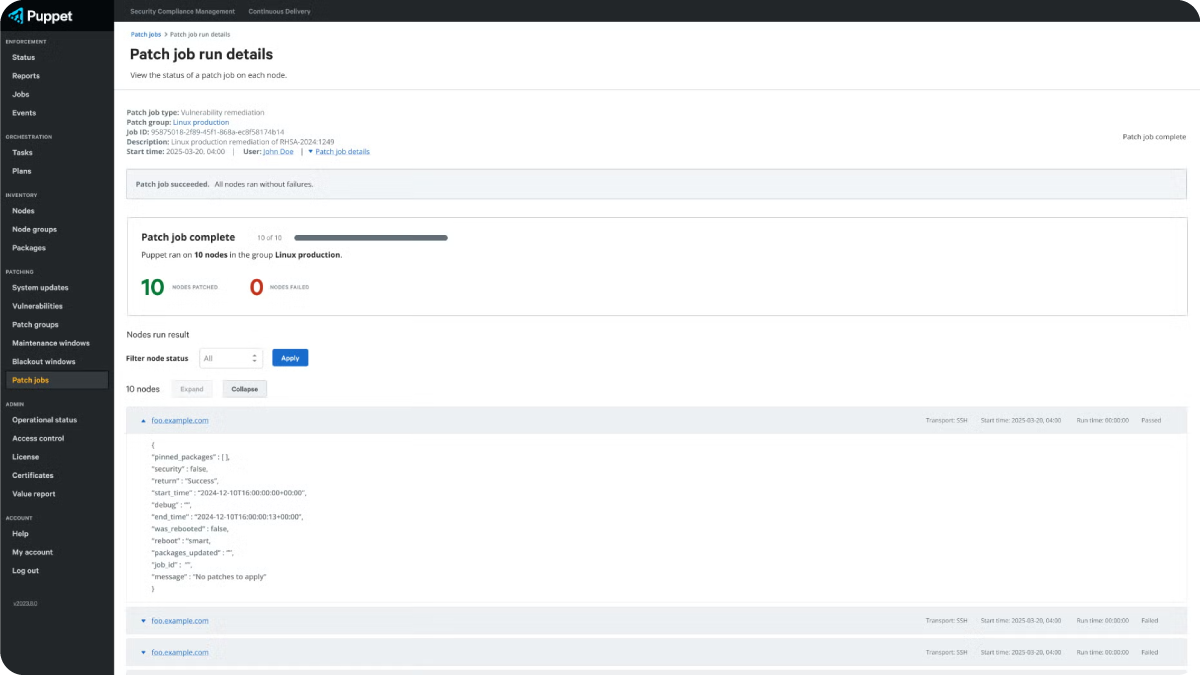
Track & Report Activities
Break down silos between security and platform teams to boost efficiency and streamline cross-functional operations.
- Share information to improve efficiency between stakeholders and related teams.
- Report on patching activities to easily satisfy auditing mandates.
- Prove regulatory compliance and achieve business-critical SLAs.
Learn More About Vulnerability Remediation in Puppet Enterprise Advanced
Vulnerability Remediation is available exclusively in Puppet Enterprise Advanced. For more information, fill out the form here to get in touch with the Puppet team.