You’re scaling your IT infrastructure so you can do more — deploying across clouds and data center, adding servers, coding like crazy. Great! But how do you keep it all from falling apart? Policy as code is an approach to managing IT that strategically leverages infrastructure as code (IaC) and compliance as code to manage consistent policies across complex IT environments.
Sounds perfect, right? But there’s no single way to go about actually using policy as code, which can make it seem harder to utilize than it actually is. Read on to get ready to use policy as code (PaC) with an explainer, a list of common policy as code tools, and example use cases for policy as code that make your infrastructure resilient and repeatable at scale.
What is Policy as Code (PaC)?
Policy as code (PaC) is an approach to IT operations and software development that represents rules, best practices, and compliance standards as code (leveraging languages like Ruby, Python, YAML, and others).
For years, organizations have written their corporate or organizational security and compliance policies into a static Word document, Confluence page, a PDF, or something similarly dry. With the advent of policy as code (PaC), those policies can now be committed into code, which opens up new possibilities for "shifting left" and baking security and compliance into your day-to-day operations.
Even better, these policies can be tested and enforced with automation, which helps ensure your systems and applications are compliant with corporate security and configuration policies while reducing human effort and error.
Back to topPolicy as Code Examples & Use Cases
Examples of policy as code include standardizing many aspects of IT operations, from compliance and security to infrastructure management, cost reduction, and code quality control.
The versatility of PaC makes it a beneficial strategy for establishing and enforcing policies across large and complex IT. PaC can be used to ensure consistency, repeatability, scalability, compliance, security, drift correction, and more common issues in the world of IT ops, like cloud misconfiguration.
Policy as code is used to maintain consistent configurations across complex infrastructure, with use cases in compliance, security, managing cloud configurations, and scaling infrastructure.
Here are a few specific use cases and examples of ways to use PaC:
Policy as Code Example: Security
An operator can write code that enforces specific encryption settings and role-based access controls. A policy as code solution will apply and enforce that code, as well as report on the impact of any code change prior to release as part of your CI/CD pipeline. For example, PaC establishes requirements for encryption and role-based access control (RBAC) configuration, and infrastructure as code defines configurations and encryption settings.
Policy as Code Example: Compliance
Compliance automation tools like the Puppet suite leverage policy as code to enforce server configurations that are compliant with PCI DSS, HIPAA, SOX, DISA STIG, CIS Benchmarks, and more. For example, you can write PCI DSS compliance policies with Puppet, then integrate those policy checks into your CI/CD pipeline so any code changes will be checked against the policy you’ve written.
Policy as Code Example: Provisioning & Managing Cloud Resources
Policy as code can define policies for cloud security, cost control, and cloud compliance. That gives infrastructure as code (IaC) a blueprint for building cloud resources according to the policies you’ve written as code. It also reduces the risk of cloud misconfiguration to make sure your infrastructure stays consistent across multi-cloud and hybrid deployments.
Policy as Code Example: Scaling Infrastructure & Maintaining Consistency
Policy as code is ideal for scaling infrastructure across environments. The policies you write using PaC can be updated easily to accommodate changes to security policies and resource configurations.
Back to topPolicy as Code Benefits
Policy as code has many benefits for IT organizations, from central IT and ops to the app layer. It’s a high-level, readable, easily understood way to state policies that enable version control and automation from provisioning to testing and deployment.
Despite 'code' being a bad word in some parts, most tools that offer PaC solutions are written in a very human readable language with the added benefit that what is written is executable and can be acted upon.
Here are a few specific benefits of policy as code:
- It offers abstraction for enforcing policies. Policies written as code are reusable across your IT environment. That means your team can use them without requiring knowledge of the particular operating systems where those policies will be deployed.
- It makes for easier testing. Policy as code expresses policies as scripts and config files, which can be automatically tested for policy violations. It also means they can be integrated into CI/CD pipelines to test before merging.
- It enables faster deployment. With PaC, compliance checks, consistency, testing, approvals, and error handling are integrated into your deployment pipeline.
- It makes configuration drift less of a problem. Systems deployed with PaC can be automatically audited for compliance. When you’re scanning for drift regularly, you can catch it early — and managing compliance suddenly becomes no big deal.
PaC vs. IaC: The Difference Between Policy as Code and Infrastructure as Code
The main difference between policy as code (PaC) and infrastructure as code (IaC) is that PaC is a set of guidelines for your IT environment, and IaC is the actual code used to build and manage infrastructure based on PaC rules.
PaC and IaC are defined by what they do, how they do it, and their use cases in setting and enforcing desired state in an IT system.
- What they do: PaC sets rules and guidelines for the way your IT environment should run. IaC creates resources in accordance with those rules.
- How they do it: PaC is all about what should be done in your IT systems and how, like a rulebook or checklist. IaC executes on that rulebook.
- How they’re used: PaC is used to define safety, compliance, and consistency in your IT environment. IaC takes those definitions and uses them to build and scale systems.
PaC is a set of rules for using IaC to build infrastructure according to the standards you’ve set for your IT environment. In contrast, IaC is a practical implementation of automation to provision and configure those resources.
Are Policy as Code and Infrastructure as Code Interchangeable?
Policy as code (PaC) and infrastructure as code (IaC) are similar, but not interchangeable. Policy as code refers to the strategy of using code to enforce policy, while infrastructure as code is the actual execution of those strategies.
The line between PaC and IaC isn’t always clear, and sometimes depends on your outlook. There are two different approaches to policy as code. One method is to use separate tooling for PaC and IaC — for example, using Sentinel inside Terraform to validate and enforce policy against Terraform projects trying to be deployed.
The other method is having policy code defined alongside your infrastructure as code. An example of this approach would be setting a password length rule in a common profile that is applied to all systems. That way, all configuration, be it security or otherwise, is all managed through the same workflow.
Back to topPolicy as Code Tools
Common policy as code tools include infrastructure provisioning tools (like Puppet, Ansible, Terraform), CI/CD tools (like GitLab), and policy enforcement tools (including Puppet, Chef, Open Policy Agent, and more).
Strictly speaking, PaC isn’t a specific tool or piece of software. Policy as code tools include different languages and pieces of software that can define and enforce policies in infrastructure code. In fact, several popular automation, configuration management, and CI/CD tools offer capabilities that can help build a PaC approach.
Puppet Enterprise can define, test, and enforce policies as human-readable expressions. Puppet policy as code allows IT operations managers to enforce policy across complex infrastructure, including public and private cloud, data centers, and hybrid infrastructure as human-readable expressions.
Policy as Code Tool | Description | Distribution (free/paid) |
|---|---|---|
Puppet | Strong agent-based configuration management, declarative language, desired state automation, extensive reporting, modularity, and compliance auditing capabilities. | Open Source Puppet (free), Puppet Enterprise (paid), Puppet Enterprise Advanced (paid) |
| Platform-agnostic, supports multiple cloud providers, large community, modular, declarative. | Open source (free), commercial version (HashiCorp Enterprise) |
Ansible | Simple YAML syntax, agentless, powerful for configuration management and orchestration. | Open source (free), commercial version (Red Hat Ansible Automation Platform) |
Can define and test compliance and security policies as code to support complex infrastructure. | Open source Chef InSpec (free), commercial version (Chef Automate) | |
SaltStack | Real-time event-driven automation, high scalability, supports a variety of OS. | Open source (free), commercial version (SaltStack Enterprise) |
AWS CloudFormation, AWS Config | Native to AWS, tightly integrated with AWS services, declarative, automated provisioning. | Free with AWS (pay for resources provisioned) |
AWS Config | Exclusively for enforcing, monitoring, and auditing policies in AWS cloud resources. | Free tier (1,000 configuration items/mo.), paid tier (scales with items, snapshots, rules) |
Pulumi | Supports multiple languages (JavaScript, Python, Go, etc.), flexible, cloud-agnostic. | Open source (free), commercial version (Pulumi Enterprise) |
Azure Resource Manager (ARM) | Exclusively for Azure. Declarative language, integrates deeply with Azure services. | Free (only for Azure usage) |
Vagrant | Ideal for creating reproducible development environments, integrates with multiple providers. | Open source (free) |
Kubernetes YAML | Native to Kubernetes, declarative syntax, large community, widely used for managing clusters. | Free (open-source Kubernetes) |
Terraform Cloud | Provides collaboration and governance, runs on HashiCorp’s cloud infrastructure. | Free (basic), commercial version (Terraform Cloud Team/Enterprise) |
Open Policy Agent (OPA) | can enforce policies across a cloud-native tech stack (like Kubernetes, cloud CI/CD pipelines, cloud security, etc.). | Free and open source (Apache 2.0) |
HashiCorp Sentinel | A policy as code framework integrated into Terraform to ensure policies are enforced during the infrastructure provisioning process. | Free and open source (limited functionality), commercial version (with features like policy testing and governance) |
GitLab CI/CD | Allows you to define and enforce policies for code quality, security scans, and deployment approvals. | Free and paid tiers |
Your policy as code will probably leverage at least two of the tools above, if not more. The PaC tools you choose should be based on where your infrastructure is hosted (cloud or on-prem or both), what kind of resources you need to manage, and your security and compliance commitments (industry frameworks, regulatory standards, etc.).
Back to topHow to Use Puppet for Policy as Code
Puppet is used to implement policy as code with automation, configuration management, and human-readable code. We like to say that with Puppet, the code is your policy — and your policy is code.
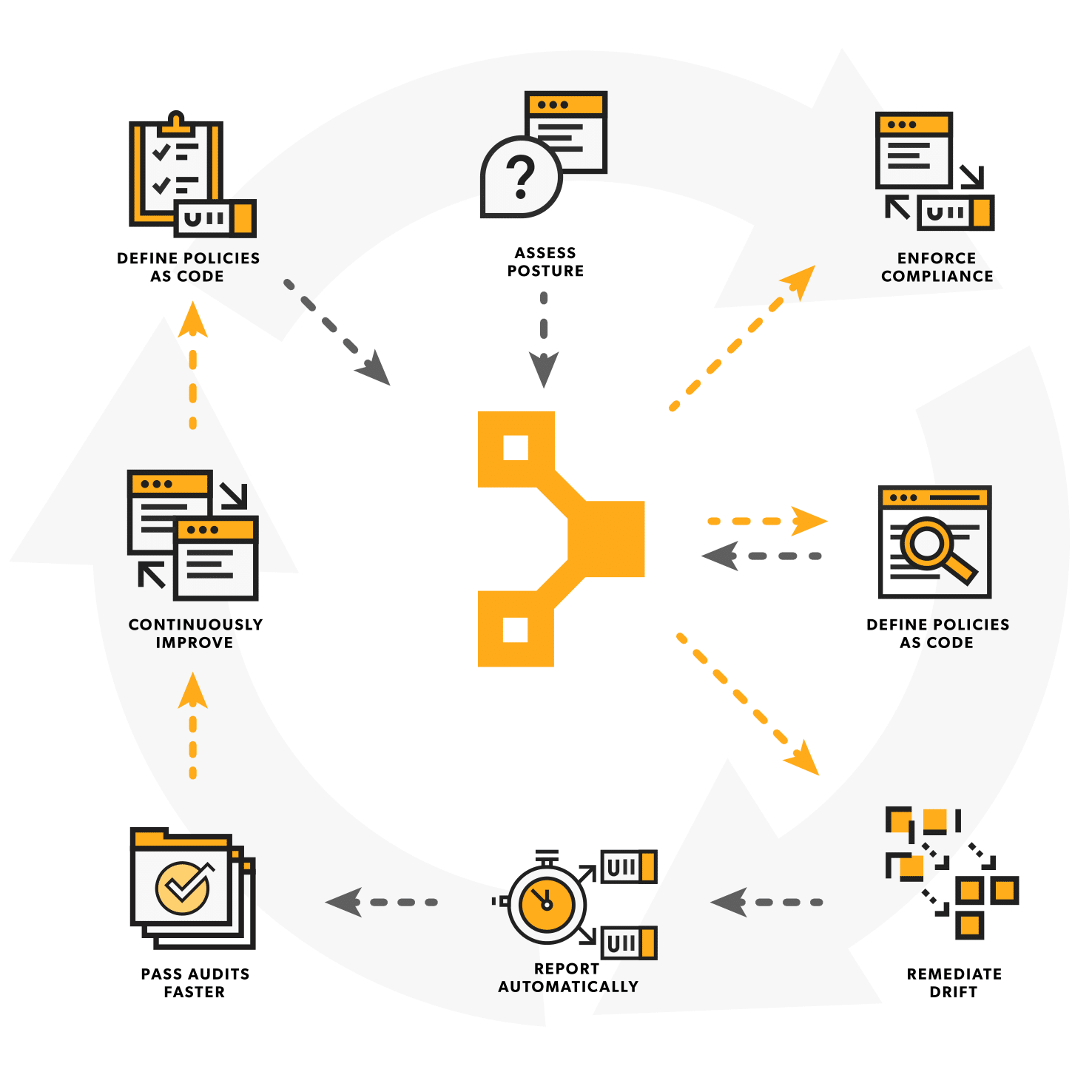
Here are a few ways Puppet can be used to establish and enforce policy as code:
- Defining policies: With Puppet, you can define security configurations, system configurations, software installs, and other components of your security and compliance policies to map out the ideal state of your infrastructure.
- Writing policies as Puppet code: Puppet’s declarative coding language means you define how you want your resources configured and Puppet will figure out how to get there. It’s all in human-readable code, too — which is essential to writing PaC that can be used and scaled by your whole team when roles and team dynamics change.
- Automating configuration management: Agents periodically connect to the Puppet server to keep configurations in your desired state. Puppet runs are scheduled every 30 minutes by default, so even if something should drift, you’re never out of policy for longer than a half hour — but you can define the frequency of Puppet runs to suit your needs.
- Provisioning cloud resources: Puppet works within the provisioning pipeline to seamlessly transition from external cloud resources (like those built with Terraform or other provisioning tools) while taking care of the OS and application layers once those resources come online.
- Monitoring systems: Puppet agents continuously monitor the state of your infrastructure, checking for deviations from your desired state as defined by your PaC. (Again, the frequency of Puppet runs is customizable, but it’s set to every half hour by default.)
- Ensuring security: With Puppet's modular style of managing code, the security team can manage security policies while the platform teams manage infrastructure settings. Then those policies can all be enforced by the Puppet agent at regular intervals, ensuring both configurations and policies are enforced at the same time.
- Achieving and proving compliance: If your infrastructure needs to comply with regulations or other compliance frameworks, Puppet creates logs that can illustrate the compliance status of your infrastructure over time (down to individual nodes). It'll also keep a record of what you did to remediate errors — both of which are essential to proving compliance and passing audits.
Puppet’s Ruby-based domain-specific language (DSL) is human-readable, making it perfect for using policy as code to keep your infrastructure consistent. It’s also trusted by thousands of companies managing millions of resources across infrastructure in the cloud, data center, hybrid, and edge. Wherever your infrastructure is, Puppet Enterprise can power a resilient policy as code approach to enforce policies at scale.
Schedule time to get a personal demo of Puppet Enterprise or try it for yourself on up to 10 nodes with the free trial edition below.