Blog
May 6, 2025
Why Patching is Important: The Risks of Ignoring It & How to Stay Ahead of Patch Management This Year
Security & Compliance,
How to & Use Cases
Let's face it: no one likes patching. For some IT ops teams, it's such a burden that it's easy to forget why patching is important. Lots of teams put off patching until it's deemed absolutely necessary, like a vital app update or a piece of critical software going EOL.
We all know ignoring patches, or letting them pile up, is a bad practice. Read this blog to remind yourself why patching is crucial, what can happen if you don't patch, and how to stop putting it off.
Why is Patching Important?
Patching is important because it fixes software and app vulnerabilities that can leave you open to cyberattacks. Patches also keep your software and apps up-to-date with the latest improvements and optimizations, leading to better performance, new capabilities, and less downtime.
Statistics that Prove the Importance of Patching
As I said, patching is such a common burden that it’s easy to forget just how vital it is to smooth, resilient IT operations. Luckily, there’s been a lot of research (and a handful of high-profile incidents) that prove why a robust vulnerability management program is essential. Here are a few:
- Zero-day vulnerabilities have an average life expectancy of 6.9 years.
- 60% of breaches are attributed to unpatched vulnerabilities.
- The average cost of a data breach in 2024 was $4.88 million USD.
Why Patching is Especially Important in the AI Era
The rise of AI will impact cybersecurity in a number of ways, including patching. Using AI to defend systems will make vulnerability identification faster and remediation easier, but the volume and frequency of threats will also increase.
There are two broad reasons AI makes patching more critical than ever. The first is about the creation of vulnerabilities in new code, and the second is about how quickly they can be exploited:
Developers are going to be using AI to help code, including for tools you use or have dependencies on, and that code is going to contain exploitable errors.
In February 2025, researchers found exploitable weaknesses in a majority of the code generated by a large language model (LLM). Another experiment found security weaknesses in more than a quarter of the code snippets generated by Copilot.
While many of these issues might be caught by automated testing and human intervention before they get baked into software you use, the fact that they’re appearing at all means patching quickly and accurately is going to be even more critical than before the advent of generative AI.
Attackers are going to use AI to exploit vulnerabilities in your systems.
I’ve written before about the good and bad of AI for cybersecurity. Long story short: It can be a double-edged sword, with one side pointing at your attackers and one pointing right back at your systems.
In the hands of an attacker, AI can work to exploit vulnerabilities faster than ever before. In one study, LLM agents exploited 13 of 15 CVEs in a system using just the CVE descriptions. Leading vulnerability scanners found 0.
Back to topThe Risks of Putting Off Patching
Failing to apply patches quickly and regularly can lead to exploits, breaches, compliance errors, supply chain liabilities, increased toil, decrease productivity, and unplanned system downtime.
As any environment grows and diversifies, it becomes more challenging and time-consuming to ensure that it is kept up-to-date and current with the latest software releases. Patching manually is inconvenient — and delaying it is downright dangerous. Inconsistent patching in a big, diverse IT environment leads to problems rolling out application updates, challenging audits, and more.
Delaying patching can have many negative consequences for an organization, including:
- Vulnerability Exploits: Cybercriminals actively monitor the release of patches and develop exploits for systems that remain unpatched. That significantly heightens your risk of cyberattacks, including data breaches.
- Zero-Day Exploits: Attackers often reverse-engineer software updates to identify weaknesses in new software versions, which means they could be exploiting vulnerabilities you don’t even know exist yet.
- Data Breaches: A successful exploit can lead to data theft, exposure of intellectual property (IP), or leakage of customer and employee records and personally identifiable information (PII), resulting in significant financial and reputational damages.
- Operational Disruption: Unpatched vulnerabilities (and attacks that exploit them) can cause system failures, corrupted files, or forced shutdowns. These disruptions can cause delays and reduce productivity.
- Compliance Failures: Almost every compliance regulation and framework requires timely patching, from GDPR and NIST to HIPAA and PCI DSS. Non-compliance due to delayed patches can result in hefty fines, penalties, and loss of security certification.
- Supply Chain Impact: If your system is breached, it could serve as a gateway to compromise partners or suppliers, damaging critical business relationships. Similarly, if a vulnerability in a piece of software you rely on is exploited, it could compromise your system hardening efforts and lead to compliance violations and broken SLAs with customers and vendors.
- Escalating Remediation Costs: Waiting to address vulnerabilities often results in more extensive damage, requiring costly forensic investigations, legal fees, and system recovery efforts (not to mention extensive manual effort and toil). Getting ahead of patching, rather than scrambling to fix things once they go wrong, significantly reduces the financial impact of remediation.
- Damage to Reputation: A successful cyberattack resulting from unpatched software erodes customer trust and damages an organization's reputation. Customers, partners, and shareholders may lose confidence in the business's ability to protect its assets and data.
- Legal Liability: Organizations that knowingly fail to patch critical vulnerabilities could face lawsuits, especially if a breach impacts customers, employees, or partners.
- Decreased Resiliency: In the modern era, many organizations (and even newer regulations like DORA and NIS2) are emphasizing resiliency — that is, not only minimizing the chance of an unplanned outage but accelerating recovery if something negative does occur. Ensuring your systems are using supported and patched software versions makes it easier to build and prove that resiliency.
These examples illustrate the breadth and depth of risks associated with ignoring patching (or just handling it manually). Having a strategy that incorporates continuous updates, rather than just responding when something goes wrong, is essential to managing a resilient IT environment.
Here’s the bad news: The longer you put off patching, the more involved and difficult patching becomes. The good news is the reverse is also true: When you make patching part of your regular routine, the easier it is to keep everything patched.
Back to topWhy Your Built-In Package Manager Can’t Solve the Biggest Challenges of Patching
Most modern organizations use a mix of operating systems across their systems (and many versions within those OSes) using the default package manager. This is challenging at any size, but it truly becomes a huge burden at scale.

Tool sprawl and bespoke patching practices alone claim a huge portion of your team’s time (hundreds of hours, by some estimates), but there are other limitations that make these built-in tools inadequate for patching enterprise infrastructure:
- Diversifying your patching tools leads to poor visibility. Out-of-the-box package managers really aren't designed for reporting. Collecting data on what resources are patched and what aren't, even on a single OS, is a manual process. Consolidated reporting across operating systems and versions is nearly impossible.
- Scheduling gets difficult with multiple tools and generally requires different orchestrators for different package managers.
If You Want to Stay Ahead of Patching, Automate It
The essential elements underpinning your patch management workflow can all be automated. In fact, the best way to enforce solid, reliable patching processes is to automate them, from scanning and testing to deploying and reporting.
Most importantly, automated patch management can keep your organization secure and compliant when your IT team is handling other priorities. A Ponemon Institute survey found that 74% of practitioners find automation valuable because it gives them the ability to focus on more serious vulnerabilities and overall security, rather than dealing manually with routine patching.
“Hundreds of thousands of hours have been saved by automated processes performing smart scans of assets, subsequently deploying patches, and remediating threats in real-time.”
Automated patch management can help solve the core issue that might lead you to putting off patching in the first place: the time-consuming, complicated nature of the task itself. Your IT team benefits from improved visibility, faster patch deployment, and less firefighting. End users also benefit because they don't have to deal with the starts-and-stops of an unpatched company network or device.
Back to topHow Puppet Makes Patch Management & Vulnerability Remediation a Non-Issue
Organizations of all sizes use Puppet for patching. DevOps and platform teams use it to orchestrate patching workflows and report on success and patching levels across your entire IT estate. You can even automate and manage end-to-end patching workflows right in the Puppet Enterprise console.
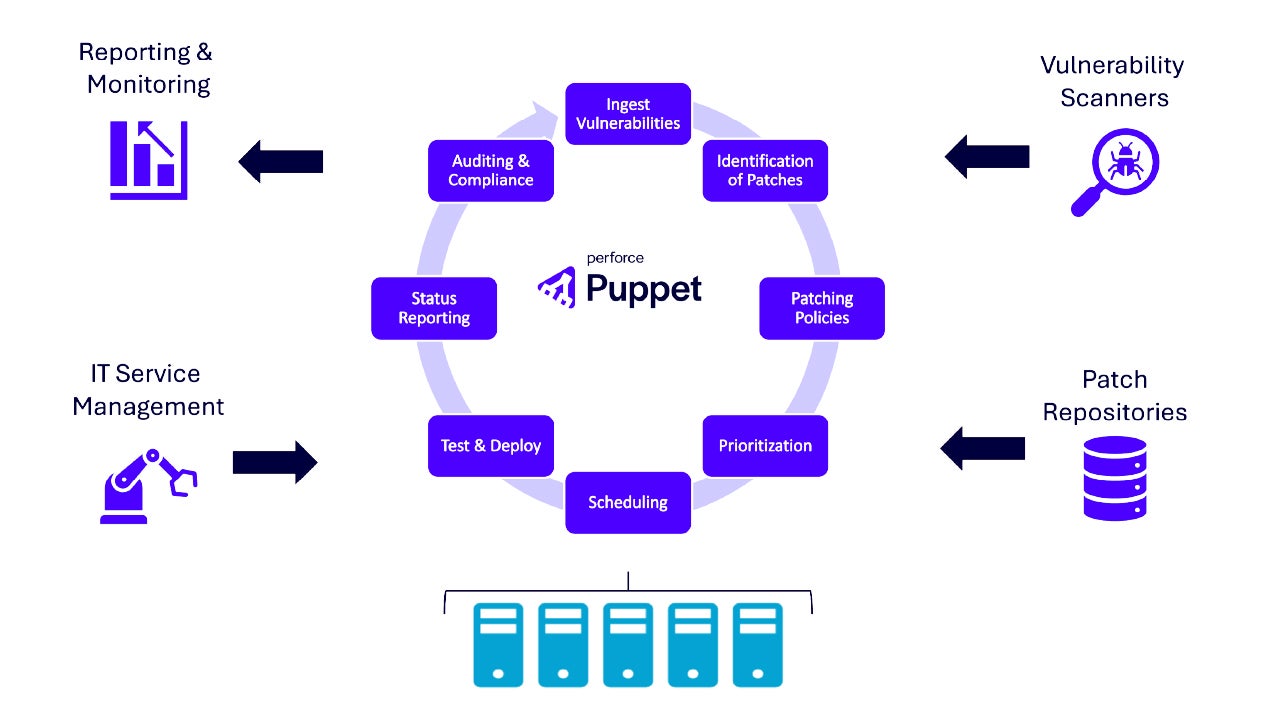
Here are some of the many reasons IT teams use Puppet to manage patching:
Define Custom Patch Groups
Patch groups (node groups dedicated to patching) are a key ingredient in the secret sauce of using Puppet for patching. With patch groups, you can choose what gets patched and when: You don’t have to choose whether to patch all of your Windows servers OR your RHEL servers at once, for example.
Patch groups in Puppet give you fine-grained control over groups of servers that you want to patch together. You can define servers in groups according to your own custom criteria, like what environment the servers are part of (dev/test/prod), instead of limiting your grouping options to things like OS.
Ingest Vulnerability Data Straight from Your Scanner
One of the biggest pain points for IT Security and Ops teams, from practitioners up to the C-level, is the lack of collaboration between teams responsible for different aspects of the patch management process. A lack of visibility is why 77% of CISOs say they struggle to prioritize vulnerabilities.
Typically, the Security team identifies a CVE and sends the information to the Operations or Platform team, often with little information or context that would help Operations know what to do with it. When it’s patched, the Operations team sends back some kind of confirmation so the Security team can close it out.
Vulnerability Remediation in Puppet Enterprise Advanced lets you connect your security scanner to your Puppet dashboard so you can feed vulnerability data right into Puppet Enterprise. Voila: Security and Operations can now see the same information on vulnerabilities. Operations can drill down into the details of each vulnerability, prioritize them individually, see what systems are affected, deploy patches, and document the change for easy reporting — all without significant Puppet coding skill via an easy-to-use GUI.
Patch Windows, Linux & More at the Same Time
Your patch groups can include servers running almost any version of Windows along with many different Linux distributions. That means you can have the Puppet agent sending information on software versions, cross-referencing it against a list of known vulnerabilities, and deploying patches to Windows and Linux as part of the same patching workflow.
Patch On-Demand or On a Schedule
The Puppet scheduler allows for unattended execution of patching, running patches on a regular schedule, and integrating patching with other regular maintenance via Puppet Tasks. The scheduler also allows you to assign the execution of patches to service desk personnel via RBAC.
Set Maintenance & Blackout Windows
Along with multi-OS patching and creating patching groups, Puppet also gives you the ability to accommodate schedules for patching as well as define when to check for new patches. When a patch is available, you can decide to deploy it immediately or schedule it for a time when users are less likely to be impacted by it.
Maintenance and blackout windows help Security and Operations teams reduce disruptions, shrink MTTR, improve the agility of their vulnerability remediation workflows, and manage more resilient IT.
Patch management helps you stay ahead of the challenges of managing diverse infrastructure at scale. There’s no better way to get started with Puppet-automated infrastructure than to leverage our patch management capabilities to stop putting off patching for good.
Learn More About Vulnerability Remediation with Puppet Schedule a Demo
