Blog
May 8, 2025
NIS2: Compliance Requirements, Deadline & Instructions for the New NIS2 Directive
Security & Compliance,
Infrastructure Automation
The compliance landscape for organisations in the European Union (EU) is heating up again — this time with the second landmark Network and Information Security (NIS2) Directive, which took effect on 17 October 2024. But what does NIS2 compliance entail? What's the difference between the original NIS1 vs. NIS2? Who needs to comply with NIS2, and what are the penalties for not complying with the new directive?
In this blog, we’ll answer your burning questions, set the record straight, and lay out your options for getting ahead of NIS2 compliance.
Table of Contents
- What is the NIS2 Directive? A NIS2 Directive Summary
- NIS2 Deadline: When Does NIS2 Come into Effect?
- Why is NIS2 Important?
- NIS1 vs. NIS2: What’s New in NIS2
- Who Does NIS2 Apply To, and Who Needs to Meet NIS2 Requirements?
- NIS2 Sectors: The Difference Between Critical & Very Critical
- NIS2 Requirements: Important NIS2 Controls & What NIS2 Means for Your IT
- What is the Impact of NIS2 on EU Businesses?
- NIS2 Timeline: Key Dates & What They Mean for You
- How to Get Compliant with NIS2 Fast & for Good
- How Puppet Automation Can Work for NIS2 Compliance
What is the NIS2 Directive? A NIS2 Directive Summary
The NIS2 Directive is an updated directive focused on creating robust cybersecurity in the European Union (EU). The purpose of the NIS2 Directive is to help EU organisations defend against cyberattacks by instituting stronger security standards in their infrastructure. The NIS2 Directive deadline was 17 October 2024.
The NIS2 Directive (sometimes styled NIS 2 Directive) requires many EU organisations to implement strong, standardized cybersecurity standards in their critical IT infrastructure.
The NIS 2 Directive affects more companies than NIS1 did and includes new penalties of up to 10 million euros and liabilities for management found in violation.
A Brief Summary of NIS2
- Expanding the scope of NIS1: NIS2 covers more industry sectors and digital service providers, including organisations and entities that weren't covered in the original NIS1.
- New fines and penalties: Entities that are found noncompliant with NIS2 could be forced to pay administrative fines of up to 10 million euros or 2% of the company's annual revenue — whichever is higher.
- New liabilities for management: If a company fails to comply with NIS2, individuals at the C-level can be held personally liable for gross negligence.
- Updated definitions for companies: NIS2 classifies organisations as "essential" and "important" instead of "operators of essential services" (OES) and "digital service providers" (DSP).
 Back to top
Back to top
NIS2 Deadline: When Does NIS2 Come into Effect?
The NIS2 Directive deadline was 17 October 2024. As of that date, the requirements of NIS2 were required to be implemented into law by each EU member state.
While the deadline remains firm, surveys from the months leading up to the deadline found that the majority of EU Member States would not be prepared to incorporate NIS2 into their laws by 17 October.
Many EU Member States missed the 17 October NIS2 deadline, including Austria, Bulgaria, Cyprus, the Czech Republic, Denmark, Estonia, Finland, France, Germany, Ireland, Italy, Luxembourg, Malta, the Netherlands, Poland, Portugal, Romania, Slovakia, Slovenia, and Spain.
Without formal transposition from their Member States, many EU organisations simply didn't know what NIS2 would mean for them as of the transposition deadline.
NIS2 Penalties
Penalties for not complying with the NIS2 Directive can carry administrative fines of up to 10 million euros (or 2% of the company’s annual revenue, whichever is higher). Failure to prove NIS2 compliance can also result in sanctions and audits.
An incident under NIS2 could also be considered a breach under GDPR, in which case NIS2 will not impose a monetary fine for that same incident. However, NIS2 may impose other non-financial penalties for the same incident.
Back to topWhy is NIS2 Important?
Back to topNIS2 is focused on three main goals: Increasing cyber resilience, streamlining cyber resilience, and improving the EU’s preparedness to deal with cyberattacks. It includes cybersecurity expectations for EU member states and consequences for failing to meet those expectations.
NIS1 vs. NIS2: What’s New in NIS2
NIS2 (2024) is the second version of the NIS Directive (introduced in 2016). The difference is that NIS2 expands into more industry sectors, adds guidelines for implementing the directive, defines penalties for noncompliance, and adds more specific language around cybersecurity expectations.
The first Network and Information Systems Directive (NIS) was introduced in 2016 as the first EU legislation on cybersecurity. NIS1, as it’s sometimes called in light of its successor, contained more room for interpretation and defined no financial penalties for noncompliance. Without a prescriptive baseline or penalties, implementation of NIS1 was inconsistent across EU member states.
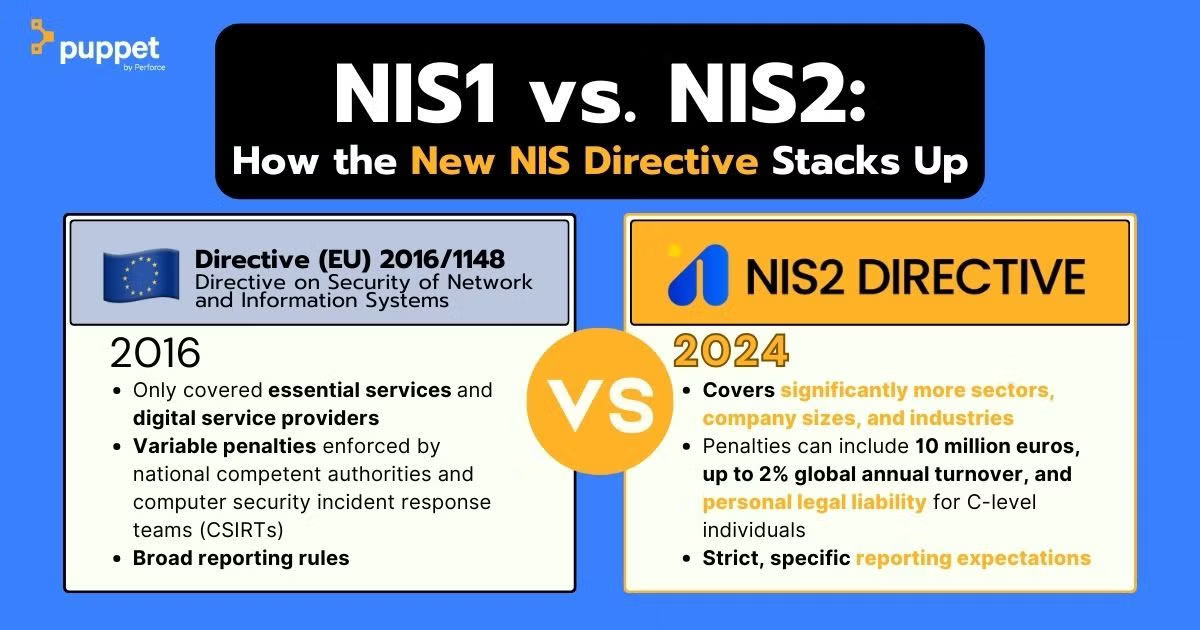
NIS2 tightens some of those gaps and standardizes requirements and definitions across member states. Here are some of the differences between NIS1 and NIS2 that highlight what makes NIS2 worth paying attention to:
More Organisations are Covered Under NIS2 Than NIS1
Many of the changes in NIS2 are intended to expand its reach beyond its direct scope by requiring mitigation of cyber risks within the IT supply chain. Specifically, NIS2 expands the scope of the original NIS to include additional industries and digital service providers. That means organisations in the EU that weren’t subject to the NIS Directive are now subject to NIS2 requirements.
Click here to jump to a list of organisations subject to NIS2 compliance >>
NIS2 Specifies Big New Penalties
On top of a widened scope, NIS2 added financial penalties not included in the language of NIS1: NIS2-noncompliant entities can be fined up to 10 million euros or 2% of the company’s annual revenue, whichever is higher.
Liabilities for Management Outlined in NIS2
NIS2 also includes more comprehensive and explicit cybersecurity requirements than NIS1. It specifically targets new governance and accountability obligations for management. Under NIS2, management bodies at entities subject to NIS2 can now be held liable if the entity fails to comply.
Individuals at the C-level can be held personally liable if they’re proven guilty of gross negligence after an incident. Member states can require organisations to publicly identify individuals responsible and, in cases of repeated violations, even ban individuals from management positions.
New Definitions Between "Essential" and "Important" Entities
NIS1’s distinction between "operators of essential services" (OES) and "digital service providers" (DSP) disappears in NIS2. It's replaced by a distinction between "essential" and "important" entities.
Back to topWho Does NIS2 Apply To, and Who Needs to Meet NIS2 Requirements?
Entities subject to NIS2 compliance requirements include businesses in critical sectors including energy, healthcare, transport, banking and finance, postal, manufacturing, digital infrastructure, and more.
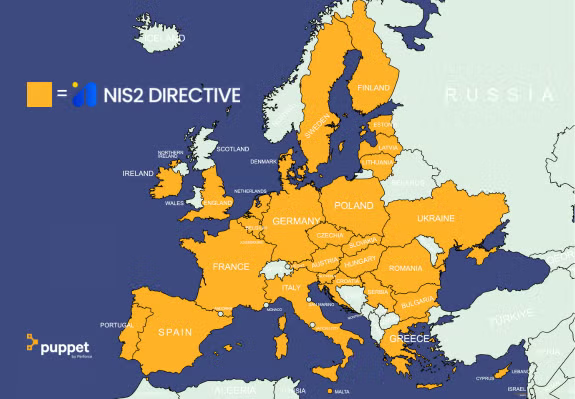
It's worth noting that NIS2 doesn't apply only to EU organisations. NIS2 can also apply to organisations outside the EU that provides services within the EU. That means that non-EU organisations that provide critical or important services to the EU (like energy, transport, healthcare, or digital infrastructure) still need to comply with NIS2.
For a list of types of organisations that need to comply with NIS2, jump to "NIS2 Sectors" below.
Map: NIS2 Countries Subject to NIS2
NIS2 Essential & Important Organisations
The NIS2 Directive classifies organisations as either “essential” or “important” entities based on their size and the criticality of the industry they exist in or the services they provide.
The exact classification of an individual organisation will depend on the role they provide in society, the economy, and dependency of other sectors. In general, NIS2 defines essential and important organisations along these lines:
- Essential organisations have more than 250 employees and an annual turnover of at least 50 million euros (or a balance sheet total of at least 43 million euros). Essential organisations will be proactively monitored to determine adherence to NIS2 legislation.
- Important organisations have between 50 and 250 employees and an annual turnover not exceeding 50 million euros (or a balance sheet total not exceeding 43 million euros). Important organisations will be subject to supervision after the fact if there are indications that an incident has occurred. Consequences may be applied if it is determined that the organisation was non-compliant.
Here’s a list of NIS2 essential and important entities, as well as their coverage under NIS1 and NIS2:
NIS2 Essential Entities
Entity | Covered in NIS1? | Covered in NIS2? |
Energy | Some | Yes |
District heating and cooling | No | Yes |
Oil and gas | Yes | Yes |
Hydrogen | No | Yes |
Transport (air, rail, water road) | Yes | Yes |
Banking | Yes | Yes |
Financial market infrastructures | Yes | Yes |
Health | Some | Yes |
Healthcare providers | Yes | Yes |
EU reference laboratories | No | Yes |
Drug research and development | No | Yes |
Basic pharmaceutical products and preparations | No | Yes |
Emergency medical devices | No | Yes |
Drinking water | Yes | Yes |
Wastewater | No | Yes |
Digital infrastructure | Yes | Yes |
Information and Communication Technology services (ICT) management | No | Yes |
Public administration | No | Yes |
Space travel | No | Yes |
NIS2 Important Entities
Entity | Covered in NIS1? | Covered in NIS2? |
Postal and courier services | No | Yes |
Waste management | No | Yes |
Chemical manufacturing, production, distribution | No | Yes |
Food production, processing, distribution | No | Yes |
Medical device manufacturing | No | Yes |
Computer, electronic, optical product manufacturing | No | Yes |
Electrical equipment manufacturing | No | Yes |
Machinery and equipment manufacturing | No | Yes |
Motor vehicle, trailer, semi manufacturing | No | Yes |
Transportation equipment manufacturing | No | Yes |
Digital providers | Some | Yes |
Online marketplaces | Yes | Yes |
Search engines | Yes | Yes |
Social networking platforms | No | Yes |
Research institutions | No | Yes |
List credit: Stibbe, “The revised Network and Information Security Directive: enhancing EU cybersecurity standards”
Back to topNIS2 Sectors: The Difference Between Critical & Very Critical
NIS2 defines sectors like healthcare, government, and digital infrastructure as “very critical,” while sectors like manufacturing, chemicals, and research are considered “critical.”
In addition to essentiality and importance, an organisation subject to NIS2 will be classified by the criticality of the sector in which it operates. Typically, only large organisations (>250 employees, >€50 million turnover) in very critical sectors are considered essential. But the distinction isn’t based only on size, industry, or sector, but a combination. For example, under NIS2, you could be a medium-sized organisation in a very critical sector and be considered important rather than essential.
Take a look at the list below for an overview of sectors considered very critical or critical under NIS2:
NIS2 Sectors: Example Industries & Businesses
Sector | NIS2 Criticality |
Energy | Very critical |
Transport | Very critical |
Banking | Very critical |
Financial market infrastructure | Very critical |
Healthcare | Very critical |
Drinking water | Very critical |
Wastewater | Very critical |
Digital infrastructure | Very critical |
ICT services management | Very critical |
Government | Very critical |
Space travel | Very critical |
Postal and courier services | Critical |
Waste management | Critical |
Chemical manufacturing, production, distribution | Critical |
Food production, processing, distribution | Critical |
Manufacturing (machinery, equipment, transportation, etc.) | Critical |
Digital providers (online marketplaces, search engines, social networking platforms, etc.) | Critical |
Research institutions | Critical |
List credit: Eversheds Sutherland, “Unlocking cybersecurity: Everything you need to know about the NIS2 directive”
Where your organisation falls in that classification matrix — essential, important, critical, very critical — will influence how and when the enforcement of NIS2 requirements occurs, what regulatory bodies enforce NIS2 compliance, and what penalties you could face for NIS2 compliance failure.
Back to topNIS2 Requirements: Important NIS2 Controls & What NIS2 Means for Your IT
NIS2 requirements include conducting risk assessments, maintaining system security, building a response plan, enforcing multi-factor authentication (MFA), reporting on compliance, and more. Requirements of the NIS2 Directive are designed to enhance common cybersecurity expectations in the EU.
Like any new compliance expectation, the NIS2 Directive requires effort to achieve and maintain. For organisations subject to NIS2 — particularly organisations with large or complex IT estates — it’ll mean more than for others.
More Resources Spent On Compliance
Organisations without a CISO will need to consider hiring one, which puts further tension on an already-strained labor market. You should also expect to spend time researching tools that can help you manage compliance in an increasingly complex compliance landscape.
Learn how compliance as code makes big compliance challenges manageable with fewer resources >>
Multi-Stage Reporting on Security & Compliance
The detailed provisions of NIS2 outline the procedure and timeline for reporting security incidents with a phased approach to ensure prompt reporting to the relevant authorities.
- Early warning (24 hours): Within 24 hours of becoming aware of a significant incident, a filing must be made to the competent supervisory authority who will respond back within 24 hours with guidance on possible mitigation measures if requested.
- Incident notification (72 hours): Within 72 hours of becoming aware of a significant incident, an update must be provided with an initial assessment of severity and impact as well as indicators of compromise.
- Final report (one month): Within one month of the incident notification, a final report must be submitted to include detailed information, its severity and impact, threat details or root cause, mitigation efforts, and cross-border impact.
What is the Impact of NIS2 on EU Businesses?
NIS2 comes with new fines, reporting requirements, and possible legal action. For many EU organisations, NIS2 will likely result in new cybersecurity measures, increased cybersecurity spend, hiring to keep up with NIS2 compliance, and additional mandatory training at many levels of the business (including leadership).
In November 2024, just after NIS2 went into effect in the EU, the European Union Agency for Cybersecurity (ENISA) published the results of a survey on NIS2 investments, gathering pre-implementation data from 1,350 organisations from every EU member state and across all NIS2 high-criticality sectors. Here’s some of what they found about the world into which the directive was released and the potential impact of NIS2 on businesses in the EU:
- 92% of organisations are aware of at least the general scope of NIS2.
- 76% of cybersecurity staff lack certified training that would help their businesses achieve and maintain NIS2 compliance.
- 89% of organisations will need to hire more cybersecurity staff to comply with NIS2.
- 34% of small- and medium-sized enterprises (SMEs) will not be able to ask for the budget they require to handle NIS2.
- Entities covered by NIS2 lag behind in compliance compared to organisations that were covered by NIS1. This includes a broad range of organisations, including ICT management, public administration, medical device manufacturing, and many more.
How heavily NIS2 impacts your business will depend on the tools, practices, and culture you adopt now. But the long haul of NIS2 only began on 17 October 2024 — and while the rollout is underway, it’s far from complete. In fact, NIS2 is likely to receive updates on key dates for the next decade and beyond.
Back to topNIS2 Timeline: Key Dates & What They Mean for You
Key post-transposition NIS2 dates include 17 January 2025 (new peer review practices); 17 April 2025 (lists of essential & important entities); and 17 October 2027 (the three-year report on NIS2 functioning).
If you’re following NIS2 as a covered organisation, you should keep the following dates in mind. Some of them will directly impact your day-to-day practices, while others could make it easier to maintain compliance by sharing new peer insight.
- 14 December 2022: The NIS2 Directive is adopted by the European Parliament and the Council.
- The new directive expanded the scope of NIS1 and laid out new expectations for cybersecurity across more kinds of companies and organisations.
- 17 July 2024: The deadline for EU-CyCLONe to submit a report on its work to the European Parliament and the Council.
- The European Union Cyber Crisis Liaison Organisation Network (EU-CyCLONe), established in 2020, supports operational coordination and management of large-scale cybersecurity incidents in the EU.
- EU-CyCLONe will be required to submit reports every 18 months thereafter. That means you can expect new EU-CyCLONe reports on or by 17 January 2026, 17 July 2027, 17 January 2029, and so on.
- 17 October 2024: Member States were required to add NIS2 to their national laws.
- Each Member State gets to decide how NIS2 becomes part of their laws, including what kinds of penalties their enforcing bodies will impose on noncompliant organisations.
- Many Member States failed to meet this deadline.
- When your Member State transposes NIS2 into law, your business will need to implement compliance policies, standards, and controls that meet those regulatory expectations.
- 18 October 2024: NIS1 is repealed and fully replaced by NIS2.
- More organisations are covered by more rules with more potential penalties.
- 17 January 2025: The NIS Cooperation Group establishes methodologies for NIS2 peer reviews.
- The Cooperation Group is made up of representatives of Member States, the European Commission, and ENISA. It’s responsible for providing guidance on transposing NIS2, sharing best practices, raising awareness, developing training, reporting, and more explicit tasks to help Member States and related bodies stay on top of NIS2. The outcome of the Cooperation Group’s peer reviews may influence how Member States implement the requirements of NIS2.
- Businesses in the EU could learn new best practices from the Cooperation Group’s work and ongoing reporting.
- 17 April 2025: Member States were required to deliver a list of essential and important entities to the European Commission and the Cooperation Group and update it at least every two years.
- Many Member States missed this deadline, and the process for delivering the lists has been uneven.
- If your organisation is classified as an essential or important entity, you should expect increased regulatory scrutiny.
- 17 October 2027: The European Commission will report on the functioning of NIS2 to Parliament and the Council.
- This report is likely to include overall compliance statistics, including percentages of covered organisations that maintain compliance and gaps in implementation, in order to plan updates to NIS2.
- Depending on the outcome of this report, your organisation could have additional NIS2 requirements after 17 October 2027.
- The European Commission will be required to submit this report every three years thereafter. That means you can expect new NIS2 updates on or by 17 October 2030, 17 October 2033, 17 October 2036, and so on.
How to Get Compliant with NIS2 Fast & for Good
As of 17 October 2024, your organisation is likely to be subject to new rules for preventing and reporting cybersecurity incidents. Luckily, there’s a lot you can do now to smooth out the process down the line.
Assess Your Current Compliance State
An organisation anticipating NIS2 must first determine if they perform business activities that will be affected. IT teams will need to work with security and audit to assess the current state of their security controls and mitigate risk in alignment with the new regulation. This can have implications that reach beyond the immediate entity due to the explicit requirement in NIS2 to address supply chain risk.
Establish IT Risk Management & Response Policies
Organisations in EU member states must establish policies that comply with NIS2, enforce them continuously, and report on incidents quickly. Here are a couple of the best practices and tools to make NIS2 compliance simpler across hybrid infrastructure:
- Risk analysis
- Policies regarding basic security hygiene (see below)
- Access controls like zero trust, role-based access control (RBAC), and multi-factor authentication (MFA)
- Cryptography and encryption
- Policies for assessing the effectiveness of risk management efforts
- Cybersecurity education and training (under NIS2, management bodies of both essential and important entities are required to undergo cybersecurity training)
- Incident response planning/crisis management
Take a look at some popular security automation tools that can make your team more proactive about compliance >>
Refresh Your Basic IT Security Hygiene
While it sounds basic, entities are expected to demonstrate good security hygiene to comply with any compliance regulation, including NIS2. Practices like establishing a cybersecurity education program, implementing backup management and disaster recovery, and testing backups can supplement established policies that assess the effectiveness of their risk management procedures.
Back to topHow Puppet Automation Can Work for NIS2 Compliance
Puppet can automate and enforce zero trust security, RBAC, MFA, compliance scanning, and configuration drift remediation across hybrid infrastructure to ensure compliance with NIS2 and other compliance expectations.
An important stage of incident mitigation and containment is to scan your infrastructure to seek out a configuration misstep. Doing this under pressure and at scale is virtually impossible without automation.
Define & Enforce Continuous Compliance, Including Popular Frameworks
Puppet can scan the infrastructure and document the current compliance state, down to each individual server. When a misconfiguration is discovered anywhere in your Puppet-managed servers, Puppet automatically remediates it to quickly bring your servers back into a compliant state.
That lets you define your own IT compliance, including by coding configurations that comply with popular security frameworks like CIS Benchmarks and DISA STIGs. That means that when you configure security standards like zero trust, RBAC, and MFA into your infrastructure using code, Puppet can routinely scan your hybrid systems and enforce the configurations from your primary server to make sure they all conform to it. Whether you’re managing hundreds of servers or hundreds of thousands, Puppet’s agent-based automation keeps it all aligned with your established policies.
Get Instant Visibility & Comprehensive Compliance Reporting
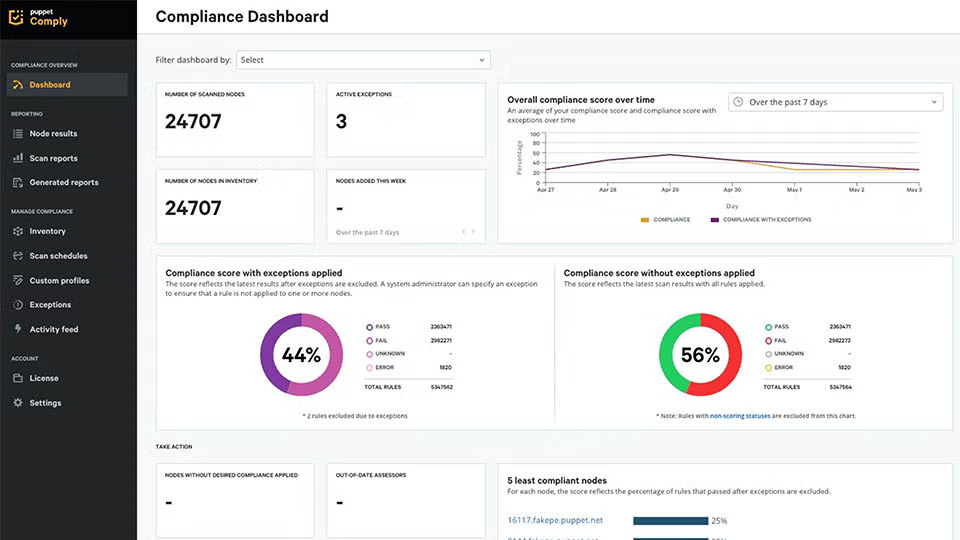
Puppet's real-time compliance reporting in action.
Additionally — and this is crucial for meeting any compliance standard or regulation — Puppet generates logs and reports of your IT compliance. When you use Puppet for compliance, you get a single pane of glass to monitor your compliance state at any time. All the documentation you need for an audit — the paper trails your team used to spend hours and days chasing down — is suddenly right at your fingertips, continuously updated and ready for auditors’ eyes.
The best way to get ready for NIS2 is to beef up your overall IT security and compliance. Request a demo of Puppet for compliance to start building the perfect Puppet plan, or download our NIS2 compliance guide for an easy-to-follow checklist and advice on using policy as code to comply with NIS2.